All about Aws Cloud Backup
Wiki Article
The Of Aws Backup
Table of ContentsFascination About Data ProtectionSome Ideas on Protection Against Ransomware You Need To KnowThe Of Data ProtectionNot known Facts About Data Protection
You can make use of firewall programs to make sure that only authorized customers are permitted to gain access to or transfer information. These procedures are normally utilized as part of an identification and also accessibility management (IAM) remedy and also in combination with role-based access controls (RBAC).Encryption secures your information from unauthorized gain access to also if data is stolen by making it unreadable. Discover more in guide to data encryption. shields portals to your network, including ports, routers, and also connected devices. Endpoint security software typically allows you to monitor your network border and to filter traffic as required.
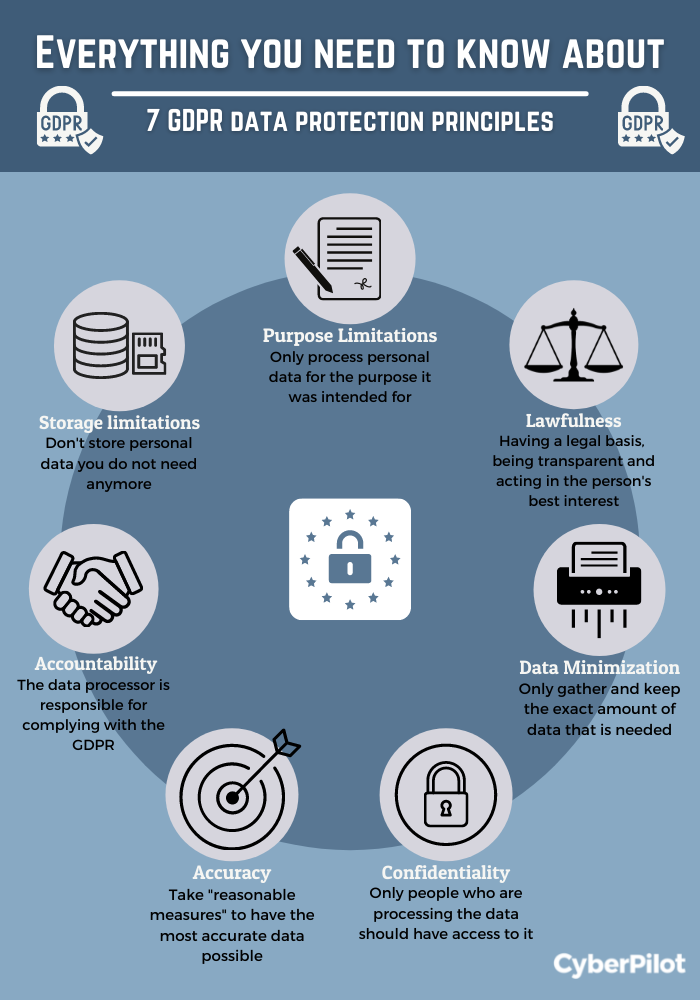
This can be done after data is refined and assessed or periodically when data is no longer appropriate. Getting rid of unneeded information is a requirement of lots of conformity laws, such as GDPR.

Top Guidelines Of Ransomware Protection
If you gather greater than what you require, you boost your obligation as well as can create an excessive burden on your security groups. Lessening your data collection can also aid you reduce bandwidth and also storage. One method of accomplishing this is to use "confirm not store" frameworks. These systems make use of third-party data to validate individuals as well as eliminate the requirement to store or transfer customer data to your systems.
Mirroring this, GDPR has actually made user approval a key element of information use and also collection. You can be certain to include customers and their authorization in your processes deliberately privacy worries right into your interfaces. protection against ransomware. As an example, having clear user notifications detailing when data is gathered and also why. You should likewise consist of alternatives for customers to modify or opt-out of data collection.
Data mobility is a crucial need for several modern IT companies. It indicates the capability to move data in between different atmospheres as well as software program applications. Extremely often, data portability indicates the ability to move data in between on-premises information facilities as well as the general public cloud, as well as between various cloud service providers. Data portability also has legal implicationswhen information is saved in different nations, it goes through different legislations and guidelines.
The Buzz on S3 Backup
This makes it challenging to relocate information from one cloud to another, and produces supplier secure. Significantly, organizations are trying to find standard means of storing and managing data, to make it mobile throughout clouds. Mobile phone protection refers to actions designed to safeguard sensitive info saved on laptop computers, smart devices, tablets, wearables and other portable gadgets.
In the modern-day IT setting, this is a vital facet of network safety. There are lots of mobile information protection devices, created to shield mobile tools and also information by recognizing dangers, developing back-ups, as well as preventing threats on the endpoint from reaching the corporate network. IT personnel use mobile data safety and security software to allow secure mobile accessibility to networks and also systems.
Ransomware is a kind of malware that encrypts user data and also requires a ransom in visit homepage order to launch it. Brand-new sorts of ransomware send the data to enemies prior to encrypting it, allowing the attackers to obtain the organization, endangering to make its sensitive information public. Back-ups are a reliable defense against ransomwareif a company has a current duplicate of its data, it can recover it as well as restore access to the information.
Facts About Rto Revealed
At this phase ransomware can infect any type of linked system, consisting of backups. aws cloud backup. When ransomware infects backups, it is "video game over" for data security approaches, due to the fact that it ends up being difficult to recover the encrypted information. There are multiple approaches for preventing ransomware and also specifically, preventing it from infecting backups: The easiest method is to make use of the old 3-2-1 back-up guideline, keeping three copies of the data on two storage space media, among which is off premises.Storage vendors are supplying unalterable storage space, which ensures that information can not be changed after it is kept. Learn exactly how Cloudian protected storage can aid shield your back-ups from ransomware. Large companies have actually multiple datasets saved in various locations, and also a lot of them may replicate information between them. Replicate data develops several problemsit enhances storage space prices, produces disparities and functional issues, and also can likewise cause security as well as compliance obstacles.
It is no usage safeguarding a dataset and guaranteeing it is compliant, when the data is duplicated in an additional unknown location. CDM is a kind of option that finds duplicate information as well as aids handle it, contrasting similar data and allowing administrators to delete unused duplicates. Catastrophe healing as a service (DRaa, S) is a handled service that gives an organization a cloud-based remote catastrophe recovery website.
With DRaa, S, any kind of dimension organization can duplicate its local systems to the cloud, as well as easily restore operations in case of a catastrophe. DRaa, S services utilize public cloud framework, making it possible to keep several duplicates of facilities as well as information throughout numerous geographical areas, to raise resiliency. Information protection requires powerful storage technology (https://rebrand.ly/izvxle6).
Report this wiki page